This is a write-up for my Banana Pi Bpi-R3 router setup.
I got this router more than a year ago but never took the time to set it up properly. It has nice features, particularly the two 2.5Gbit ports that connect my NAS to my local server for fast transfer.
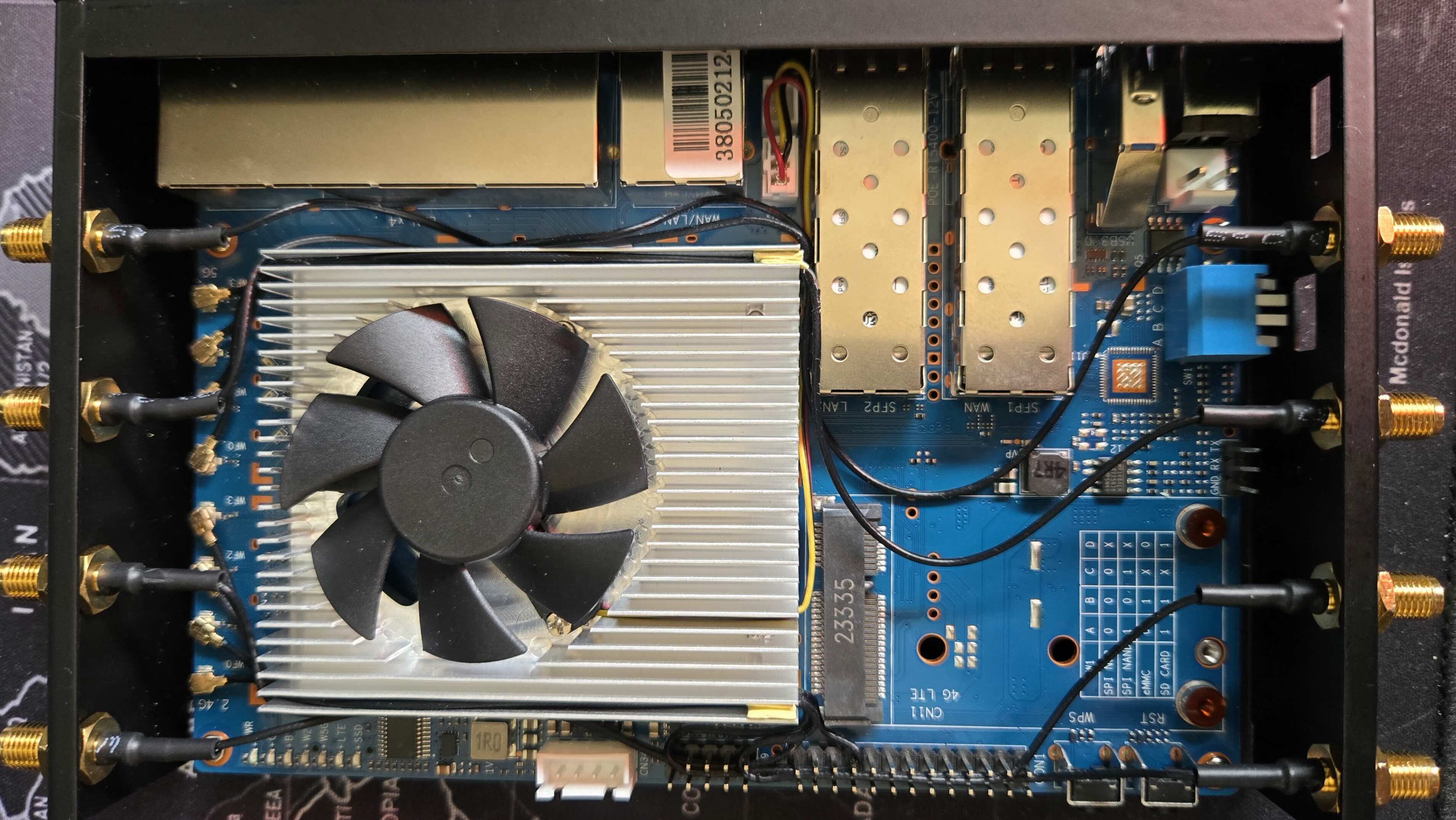
(a)My antenna wiring
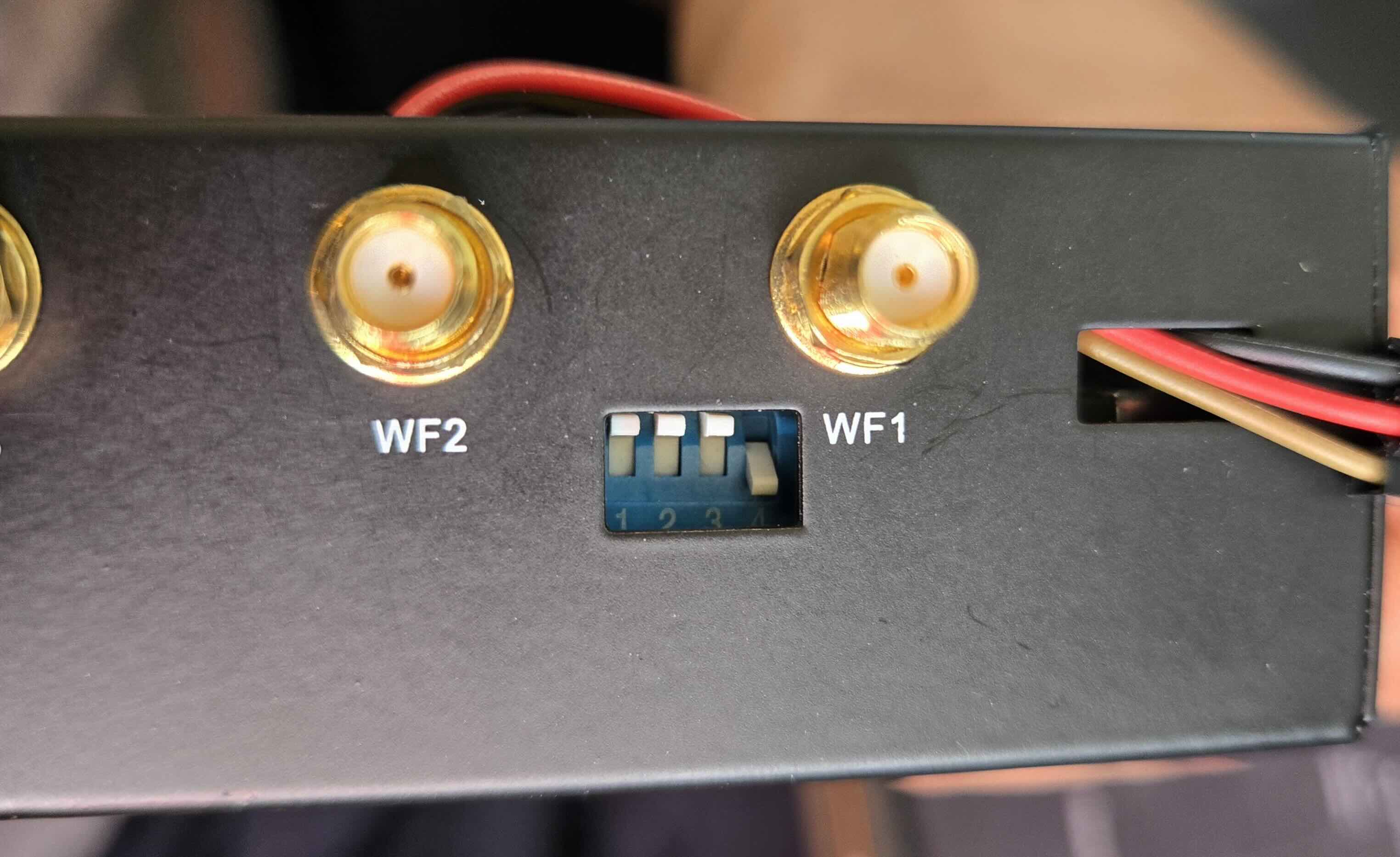
(b)Switches set to 1110
Attention
This post assumes:
familiarity with router configurations
a basic understanding of network concepts: IP, subnets, firewalls, routing, NAT techniques (masquerading)
Linux scripting
Flashing OpenWrt¶
Get the factory image (SD card) from here:
https://
Flashing to SD Card¶
Use balena-etcher or dd to write the image to the SD card. If you have access to a Serial connector to choose the boot menu option, that is good. If not, we are going to do it the hard way. This requires a PC with an ethernet connection. First:
Flip all the white switches up (A=B=C=D=1), and insert the SD card. This will boot the image from the SD card while giving access to NAND (C=1).
Flashing to EMMC¶
Once powered on, SSH into the router (user: root, no password) and do:
fw_setenv bootcmd "env default bootcmd ; saveenv ; run ubi_init ; bootmenu 0"
rebootThis should write the image to NAND memory (128MB capacity) on reboot.
Remove the SD card (for safety). Now switches should be A=1, B=0, C=1, D=0 to boot from NAND.
Again, SSH into the router (if you get host key issues, just do
ssh-keygen -R 192.168.1.1to reset them), and run:
fw_setenv bootcmd "env default bootcmd ; saveenv ; saveenv ; run emmc_init ; bootmenu 0"
rebootThis should set the default boot option to write the image to EMMC. At this level, the EMMC partitions reflect NAND, but EMMC has 8GB of space, so we need some resizing:
opkg update
opkg install parted block-mount lsblkThen run:
parted /dev/mmcblk0 printIf asked to fix the GPT table, say yes.
Now we will add partition 6 that takes all available space:
parted /dev/mmcblk0 -- mkpart f2fs 768MiB -34s resizepart 5 768MiB resizepart 4 67.1M resizepart 3 12.6MWith parted ... print, it should be visible now.
Then do:
mkfs.f2fs -l data /dev/mmcblk0p6
block info
# > /dev/mmcblk0p6: UUID="94c379b9-712d-4251-9307-ccb2693e5527" LABEL="data" VERSION="1.16" TYPE="f2fs"
# > /dev/fitrw: UUID="f387e1d4-1088-4b12-bec4-a417e16eae3d" LABEL="rootfs_data" VERSION="1.16" MOUNT="/overlay" TYPE="f2fs"Switch to ABCD=0110, reset to boot from the EMMC partition, and get some basic networking setup (Wifi, LAN...).
Now we have a backup image in the NAND. In case something goes kaput, we use the switches as 1010, and we’re back to business.
Data Partition Storage Tricks¶
After booting from EMMC, the following packages will enable some mounting settings in LuCI (UCI web interface):
opkg update
opkg install parted block-mount lsblkOur goal now is to mount /dev/mmcblk0p6 as /data:
DEVICE="/dev/mmcblk0p6"
MOUNT="/data"
eval $(block info ${DEVICE} | grep -o -e 'UUID="\S*"')
echo Got UUID=$UUID for MOUNT=$MOUNT
# Add fstab entry
uci -q delete fstab.data
uci set fstab.data="mount"
uci set fstab.data.uuid="${UUID}"
uci set fstab.data.target="${MOUNT}"
uci commit fstab
# check uci fstab
uci show fstab
rebootNow /dev/mmcblk0p6 is mounted as /data. On the GUI (go to IP of the router), go to System -> Mount Points to see all mounts.
We can also use the partition as the overlay or add SD card/USB drives following the official guide:
https://
Some Tweaks¶
Persistent Package List¶
If you have enough space on the overlay, in /etc/opkg.conf, replace list_dirs /var/opkg-lists with list_dirs /usr/lib/opkg/lists then run:
opkg update
ls /usr/lib/opkg/listsSFP for LANs¶
As I mentioned, I don’t want to use SFP1 for WAN, so in Network -> Interfaces -> Devices remove br-wan... only keep wan and br-lan. Then configure br-lan to include SFP1, which is named here as eth1. Then, on Network -> Interfaces, make sure wan uses the wan device (instead of br-wan). Reboot.
Fan Always On (Max Speed)¶
I got the official cooler, and it’s not noisy at all at full speed. So let’s change the rc file to:
#/etc/rc.local
# Put your custom commands here that should be executed once
# the system init finished. By default this file does nothing.
# 0 -- max speed
echo 0 > /sys/devices/platform/pwm-fan/hwmon/hwmon1/pwm1
exit 0Wireless Ethernet Dispatch¶
For OpenWrt 24.10:
# /etc/modules.conf append
options mt7915e wed_enable=YThis should add a statistics tab to LuCI:
opkg install luci-app-statistics collectd-mod-thermal luci-app-temp-statusRouting¶
I have a NAS running at 10.0.1.2, and it has a docker subnet with various containers on 10.10.0.0/24.
The full chart of my network is as follows:
To allow my LAN devices to reach the docker subnet:
Network->Routing->Static IPv4 RoutesUnicast, Target:
10.10.0.0/24, Gateway:10.0.1.2
The NAS server should be configured to do the forwarding. Since I’m using Unraid OS, on /boot/config/go, add at the top:
iptables -I DOCKER-USER -s 10.0.1.0/24 -d 10.10.0.0/24 -j ACCEPTNote: Using VPN on a client might hijack the static routes.
Integration with ZeroTier¶
First, you should check zLAN: Worldwide LAN via Zerotier.
OpenWrt has a package for ZeroTier. The nice thing about this is that once the router is part of the ZeroTier network, we can set routes so that the LAN devices can reach ZeroTier clients via static routing, the same way we did with the docker subnet.
Make sure to add the routes in the ZeroTier panel. In the chart, I’m routing 10.0.1.0/24 through ZeroTier’s 10.100.0.1.
Following: https://
Install with opkg install zerotier and check the existing template uci show zerotier, it should display:
zerotier.global=zerotier
zerotier.global.enabled='0'
zerotier.earth=network
zerotier.earth.id='8056c2e21c000001'
zerotier.earth.allow_managed='1'
zerotier.earth.allow_global='0'
zerotier.earth.allow_default='0'
zerotier.earth.allow_dns='0'Following the logic of previous examples of configuring using uci, we want to allow ZeroTier to set some routes:
uci delete zerotier.earth
uci set zerotier.GhriNet=network
uci set zerotier.GhriNet.id={SET YOUR ID from ZeroTier}
uci set zerotier.GhriNet.allow_managed='1'
uci set zerotier.GhriNet.allow_global='0'
uci set zerotier.GhriNet.allow_default='0'
uci set zerotier.GhriNet.allow_dns='0'Once uci show zerotier looks good:
uci set zerotier.global.enabled='1'
uci commit zerotier
rebootConfirm the device appears on the ZeroTier control panel. I’m using the old control panel; the new one does not seem to have the managed routes setting.
Bridging LAN with zLAN¶
Network->Interfaces->Add New InterfaceName:
zlan, Protocol:unmanaged, Device:z.*device
We now need to allow traffic between LAN and zLAN:
Network->Firewall->Zones->Add:Name:
zerotier, Input:Accept, Output:Accept, Forward:Accept, Masquerading:No, Covered:zlanAllow forward to destination:
lan, Allow forward from source:lan
Reboot and check by pinging 10.100.0.101 from a Central LAN device. Make sure the device used to test is not
connected to ZeroTier to force the router’s routes.